FAQs
- Home
- FAQs
AVG Management
Een verwerking is alles wat er met persoonsgegevens kan gebeuren. Wanneer er persoonsgegevens worden ingezien, bewerkt, verwijderd, opgeslagen of anderzijds behandeld worden ze dus verwerkt.
Een persoon, bedrijf of overheidsinstantie die bepaald hoe en waarom er persoonsgegevens verwerkt worden. Dit kan gezien worden als de opdrachtgever (verwerkingsverantwoordelijke) en opdrachtnemer (verwerker).
Verwerkers zijn personen, bedrijven of overheidsinstanties die in opdracht van de verwerkingsverantwoordelijke persoonsgegevens verwerken. Dit mag enkel gebeuren voor de door de verwerkingsverantwoordelijke gestelde doelstelling.
Subverwerkers zijn verwerkers die zijn ingehuurd door de verwerkers waarbij de verwerkingsverantwoordelijke verantwoordelijk is voor de (sub)verwerkers.
U bent wettelijk verplicht een PIA uit te voeren als:U systematisch persoonlijke aspecten van een natuurlijk persoon evalueert (hier valt ook profiling onder), U op grote schaal bijzondere persoonsgegevens verwerkt, U (bijvoorbeeld via cameratoezicht) op grote schaal en systematisch mensen volgt. Zelfs wanneer u niet wettelijk verplicht bent om een PIA uit te voeren kan het nuttig zijn om dit alsnog te doen. U krijgt hiermee een goede indruk van welke risico’s er gepaard gaan met een bepaalde verwerking.
De rechten van betrokkenen houden in dat betrokkene vanaf mei 2018 : Inzage kunnen vragen in de persoonsgegevens die bedrijven over hun verwerken (mits dit geen onredelijke last legt op het bedrijf) (recht op inzage), bedrijven mogen vragen om correctie als de betrokkene een fout ziet/merkt in de aangeleverde persoonsgegevens (recht op correctie), bedrijven mogen vragen om een uitdraai van de gegevens die bedrijven over ze hebben (recht op dataportibaliteit. Bedrijven mogen vragen of ze de persoonsgegevens die ze van de betrokkene hebben willen verwijderen (recht op vergetelheid). Dit laatste recht houdt in dat niet alleen het bedrijf dat de persoonsgegevens van de betrokkene heeft ontvangen het moet wissen, maar ook alle bedrijven waaraan de persoonsgegevens zijn aangeleverd (subverwerkers, uitbesteden email campagnes etc).
Een verwerking is alles wat er met persoonsgegevens kan gebeuren. Wanneer er persoonsgegevens worden ingezien, bewerkt, verwijderd, opgeslagen of anderzijds behandeld worden ze dus verwerkt.
De AVG stelt dat er 2 begrippen centraal moeten staan bij het verwerken van persoonsgegevens: “Privacy by design” en “Privacy by default”. De Autoriteit Persoonsgegevens (AP) beschrijft “Privacy by design” als volgt: “Privacy by design houdt in dat u als organisatie al tijdens de ontwikkeling van producten en diensten (zoals informatiesystemen) ten eerste aandacht besteedt aan privacyverhogende maatregelen, ook wel privacy enhancing technologies (PET) genoemd. Ten tweede houdt u rekening met dataminimalisatie: u verwerkt zo min mogelijk persoonsgegevens, dat wil zeggen alleen de gegevens die noodzakelijk zijn voor het doel van de verwerking. Op deze manier kunt u een zorgvuldige en verantwoorde omgang met persoonsgegevens technisch afdwingen.” Privacy by Default houdt in dat de standaardinstellingen van programma’s of diensten al standaard staan ingesteld op maximale privacyinstellingen. Uitgangspunt is hierin dat de betrokkene zonder (verborgen) instellingen aan te passen toch de maximale privacy geniet.
Een datalek is een inbreuk op beveiliging die ertoe leidt dat er ongeoorloofde toegang, wijziging, of opvragingen hebben plaatsgenomen van de opgeslagen persoonsgegevens.
Een incident is eigenlijk hetzelfde als een datalek, maar het verschil is hier dat er nog moet worden vastgesteld of er ongeoorloofde toegang is verleend die kan leiden tot opvraging, wijziging, of vernietiging van opgeslagen persoonsgegevens.
In het geval van grensoverschrijdende gegevensverwerking gaat het erom waar het hoofdkantoor van de verwerkingsverantwoordelijke staat, als die bijvoorbeeld in Nederland staat heb je eigenlijk vooral met de Autoriteit Persoonsgegevens te maken, deze is dan de leidende toezichthouder. Er zijn echter ook toezichthouders betrokken in de landen van de betrokkene(n), maar deze zullen dan met de leidende toezichthouder afstemmen wat er gedaan moet worden wat betreft maatregelen/boetes.
Wanneer u geen toegang krijgt tot de tool kunt u een aantal dingen doen: De AVG.Management Tool draait op een beveiligingscertificaat van wat voorheen Comodo was. Het kan zijn dat u een beveiligingswaarschuwing krijgt waarin verteld wordt dat de uitgever onbekend is. Wanneer dit voorkomt kunt u kijken of uw computer up-to-date is. We hebben gemerkt dat klanten met een Mac-OS lager dan 10.11 vaak die melding krijgen. U zult een software-upgrade moeten uitvoeren om deze melding in het vervolg niet meer te krijgen. Voor overige problemen kunt u een mailtje sturen naar helpdesk@avg.management.
Wanneer er een recht op vergetelheid wordt beoefend moet u rekening houden met een aantal zaken. Er zijn namelijk uitzonderingen voor het recht van vergetelheid. Het recht van vergetelheid is namelijk niet van toepassing op de volgende wettelijke grondslagen: Contractuele overeenkomst, wettelijke verplichting, vitale belangen en taak van algemeen belang. Twee dingen waar u in elk geval rekening mee moet houden zijn: De Wet op de omzetbelasting die valt onder de fiscale bewaarplicht. Dit houd in dat u alle facturen van u en uw klanten moet bewaren (Wet op de omzetbelasting Art. 35c) gedurende 7 jaar (fiscale bewaarplicht). Verder moet u onder de fiscale bewaarplicht de volgende dingen bewaren voor 7 jaar: het grootboek de debiteuren- en crediteurenadministratie de voorraadadministratie de in- en verkoopadministratie de loonadministratie Dit betekent dus dat ook wanneer een werknemer een recht op vergetelheid uitvoert u de loonstroken niet mag verwijderen tot de 7 jaar verstreken zijn. Voor de uitzonderingen op deze bewaarplicht kunt u terecht bij de bron: De Belastingdienst Dit zijn in elk geval de dingen die alle organisaties moet bewaren. Het kan zijn dat op basis van het type persoonsgegevens er ook andere bewaarplichten gelden.
Antivirus
De Antivirus Service Agent kan op de volgende besturingsystemen geinstalleerd worden op de volgende besturingssystemen:
- Vanaf Windows® 7 SP1 (Build 6.1.7601)
- Windows® 10 of hoger.
- Windows Server® 2008 R2 SP1 (Build 6.1.7601).
- Windows Server® 2012 R2 of hoger.
Applicaties:
- Microsoft Outlook® 2019.
- Windows Terminal Server.
- Sharepoint Server
Hardware:
- 2 GHz CPU,
- 2 GB RAM
- en 500 MB HDD.
Het te downloaden bestand is 46 MB en na installatie 86 MB groot
De Antivirus Service is voorzien van een automatische update functionaliteit. Set it and forget it!
De antivirus agent zorgt voor:
- Guard
- Activeer / deactiveer virus-, adware- en spambeschermingsmodules

- Update
- Overzicht van de updatestatus

- Quarantine
- Bestanden die als schadelijk zijn geclassificeerd en hoe u hiermee om kunt gaan

- Scan
- Start scannen, verander scanprofielen of maak nieuwe aan
Het wordt over het algemeen sterk aangeraden om eerst uw oude antivirus programma te verwijderen voordat u een nieuwe installeert. Dit komt omdat twee antivirus oplossingen op hetzelfde systeem elkaar erg kunnen tegenwerken en het systeem enorm kunnen vertragen.

In het dashboard van de Antivirus Service kun je het volgende beheren:
- Licentie
- Management,
- Quarantaine management,
- Management van client settings,
- Systeem status (dreigingen, actueel) Onafhankelijk van domeinen en locaties,
- Waarschuwingen

De Antivirus Service voor Android toestellen is in de prijzen gevallen als sterk presterende antivirus oplossing voor Android. Het beschermt proactief je telefoon of tablet tegen malware in apps en van het internet. Deze door Ikarus Security zelf ontwikkelde technologie leent zich uitstekend voor de beveiliging van je mobiele apparaten.Vind en verwijderd allerleid soorten malware zonder merkbare impact op je batterij-levensduur of geheugengebruik. Met een betaalde versie beschik je over meer functies zoals privacy controle en SMS Blacklisting.

Besturingsystemen
- Android version 4.1 of hoger,
- Android version 4.1 of hoger,
- Android smartphone of tablet
Zolang het apparaat verbonden is met het internet zal de Antivirus Service blijven werken.

AV-Test -Android Certificatie:
- 99,2% realtime detectie van de nieuwste Android-malware,
- 99,6% detectie van de huidige Android-malware van de afgelopen 4 weken
- geen invloed op de levensduur van de batterij
- vertraagt het gebruik van het apparaat bij normaal gebruik niet
- Genereert weinig netwerkbelasting

PCSL – Android Certificatie
- Detectiepercentage van 99,9% en geen valse berichten
- 5 sterren gewonnen in de PCSL Android Malware Detection Test

- Applicaties worden getest aan de hand van lijsten met bekende kwaadaardige apps
- Applicatie-installatieprogramma's en binaire bestanden worden gescand door verschillende anti-malware-engines van de Metadefender Cloud en mogen niet vaker dan vier keer worden gemarkeerd
- Applicaties moeten volledig kunnen worden verwijderd zonder actieve functies in het systeem achter te laten

Virus Bulletin – VB100- Windows Certificatie:
- bewezen dat ten minste 99,5% van de gedetecteerde malware
- genereert niet meer dan 0,01% valse alarmen bij het scannen van een grote verzameling "schone" monsters
- voldoet aan al deze eisen met standaard instellingen in de VB-testomgeving op twee testplatforms

- Applicaties worden getest aan de hand van lijsten met bekende kwaadaardige apps
- Applicatie-installatieprogramma's en binaire bestanden worden gescand door verschillende anti-malware-engines van de Metadefender Cloud en mogen niet vaker dan vier keer worden gemarkeerd
- Applicaties moeten volledig kunnen worden verwijderd zonder actieve functies in het systeem achter te laten
Wachtwoord Management
The ID Control Password Management service is a way to generate and store unique and complex passwords. You can use the built-in password complexity checker to see how strong your passwords are. The Password Management service also provides a way to see whether your passwords have ever been found in a breach so you can rest assured that no one other than yourself has access to your passwords.
The grouping functionality is designed to make it easier for your employees to access certain systems that are important to them. Consider, for example, an HR employee who can only access groups that the HR needs access to using groups.
Using our Android and iOS apps you can access your passwords even from your mobile devices. For this you have to download the app and login to your Password Management account to access all your passwords. You can view, edit, copy and paste the passwords in your account to use in your other mobile apps.
The Security Report feature is a quick way to keep your passwords safe. You can see how strong your passwords are and you can also check if they have been leaked in a data breach. Here you can also see if you have used passwords twice or if a password is too old and should be changed.
Single Sign-On refers to a method where you can log in at a central place and not have to input your passwords at connected services. When using Single Sign-On (SSO) there is a small file that is placed on your computer (called a “cookie”) which can identify you when you surf to other websites and can automatically log you in.
In theory the use of a single username and password is indeed less secure. That is why we add an additional layer of security by requiring you to login using both a username and password and a one-time password that can be generated on a mobile phone by using SMS or a one-time password generating app, or you can purchase a small device that generates these one-time passwords that you can hang on your keychain.
The ID Control Multi-Factor authentication provides an additional layer of protection to your logon by requiring you to use something you know (your username and password) and something you have (like a mobile authenticator that generates One-Time Passwords).
With the ID Control Multi-Factor Authentication you can use the following options:
– SMS (MessageID)
– OTP generating app such as (but not limited to) Google/Microsoft Authenticator, FreeOTP or Authy
– Hardware OTP generator, this is a small device with a display that generates One-Time Passwords.
– OTP by email (MailID)
When you lose your hardware OTP generator you can login to the ID Control Strong Authentication user panel and set your token to “Lost”. You will be given a temporary password you can use instead of your OTP until you are given a new hardware token. The temporary password is valid for 10 days.
While Google Chrome and Mozilla Firefox offer the option to remember your passwords they lack the ability to generate secure passwords for you. Also when you want to access these passwords you are bound to that particular browser to use the passwords. The Password Cloud offers you the option to take the passwords with you regardless of your browser or device. Just log in to the Password Cloud using your masterpassword and one-time password and access all of your accounts!
The web interface can be reached using every browser, but when you want to autofill your passwords using our browser extension, using Firefox or Chrome is recommended.
Your passwords are protected using multiple layers of encryption, both while traveling over the internet and when stored on the server.
We use NaCl for the server and the front end (the web page from where you can login). We chose not to go with the well-known RSA and AES because even though they are well-known they are also very easy to implement wrong.
When you are using our browser plugin all your passwords are encrypted before leaving your browser and will never travel the internet in the open! When pulling a password from the server that is also encrypted until it reaches your browser. All your passwords are also encrypted while stored on the server so even the server admins can’t access them!
You can share passwords using the “Link share” functionality. This will create a link for you to send to your friend where they can see the password. You can also optionally choose to either set a password on that password link and set an expiry date or use count (for example: the link will only be able to be seen once).
Our Single Sign-On solution makes use of open standards such as the SAML standard and the OpenID standard to ensure maximum compatibility and flexibility.
This can be dependent on how the Single Sign-On is implemented. The Single Sign-On platform can import users from your office userbase (for example using Active Directory), your webserver (for example using SQL), or can be put in manually. When using your own office userbase your username and password are stored there and can be changed there.
When you purchase a service (either Password Management, Single Sign-On management or the Combi-Package) you need to create a user in the Mutli-Factor Authentication platform. When you have created that user you can assign it tokens. What types of tokens are supported are explained in “Which types of login methods are supported?”. Once the users have tokens assigned to them they can use the Strong Authentication to login to their services.
If you are using SMS based One-Time Passwords you need to enter your phone number in the Multi-Factor Authentication platform and assign yourself an SMS token. When using an OTP generating app, create a “Software token” and then scan the QR code with your Authenticator app.
If you’ve lost your mobile phone you can login to the Multi-Factor Authentication platform to set your mobile token as “Lost”. This will create a temporary password you can use instead of your One-Time Password. The temporary password is valid for 10 days.
Veilige toegang op afstand
The Remote Access Cloud is a solution with which you can surf to a website using a webbrowser of choice (for example Google Chrome, Mozilla Firefox, Opera, Edge etc) and get connected to your computer at the office.
The only thing that is required to use the Remote Access Cloud is a web browser! This way you can make use of the software whether it’s on your computer at home, your laptop on the road or your mobile phone!
The grouping functionality is designed to make it easier for your employees to access certain systems that are important to them. Consider, for example, an HR employee who can only access groups that the HR needs access to using groups.
No, the Remote Access Cloud can be used without a VPN, just log into a website using a browser of choice (Google Chrome, Mozilla Firefox, Edge etc) and start working!
Yes you can! You can configure the Remote Access Cloud to record your sessions and then disable it after your session is done.
To ensure that the computer is always available, it is useful to ensure that it does not go to sleep after a certain period of inactivity. Follow the next steps:
Press Start and type “powercfg.cpl” without quotes and press Enter.

In the next screen click Change when the computer sleeps.

In the next screen select Never at “Put the computer to sleep”.

Now click Save Changes and you’re done!
Video bellen
We recommend using Chromium based browsers for Video Conferencing.
Chromium based browsers are for example:
- Microsoft Edge
- Google Chrome
- Opera
- Brave
- Vivaldi
- and many more…
- Firefox
- Safari we would not recommend
Bleow you can find the Android and iOS Apps for mobiles and tablets:.
First confirm that your microphone is connected to your computer, after that click the 3 dots in the lower right corner of the screen to open up the More actions menu.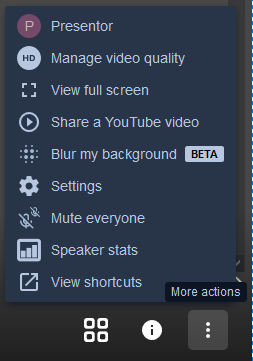
With this menu open, click on Settings. In the following dialog box you can check whether your microphone detects any input, if not, try switching to a different microphone.

1. Select the little monitor icon in the lower left corner.
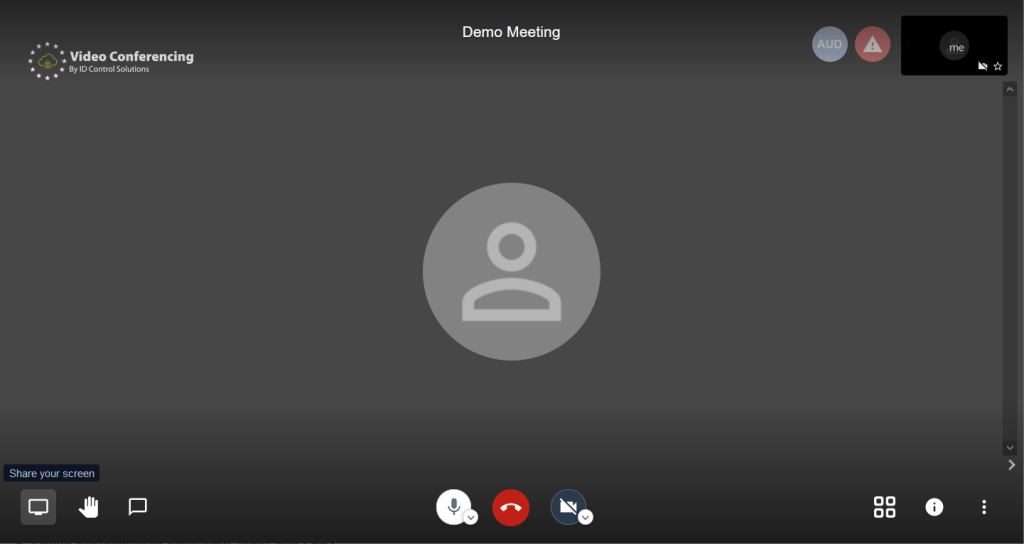
2. In the pop-up window, select the “Application Window” tab.

3. Select the Application you want to share (usually Powerpoint or PDF-Viewer)
4. Press Share (you have to click on a tile (3) to activate the ‘Share’ button)
You can of course share your entire screen (the tab most left in step 2) but then you’ll have to hide your Videomeeting window. Otherwise you get an infinite video-loop.
And you can share just a tab from the browser your Video-meeting runs in. For this pick the tab to the right.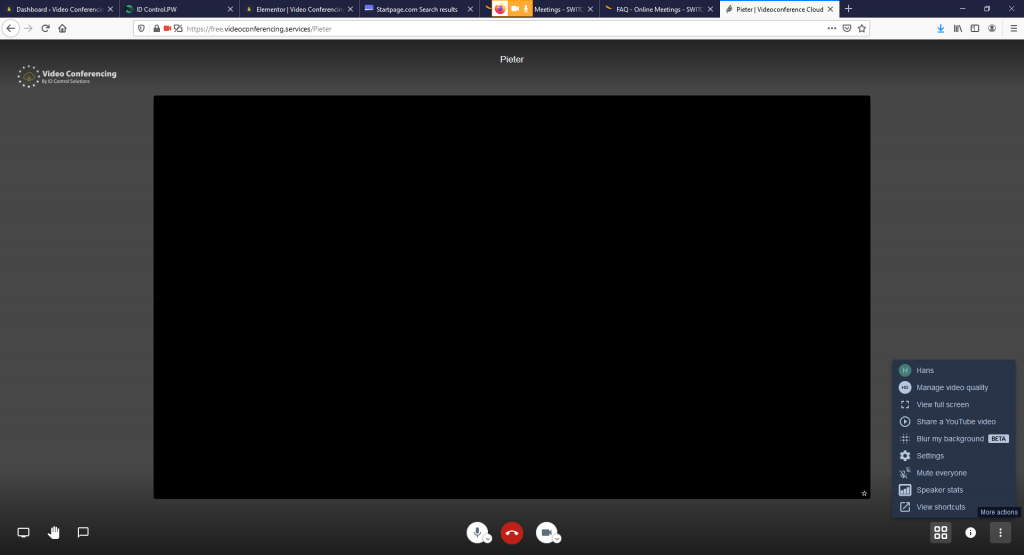
T
his is normal behaviour. Only 3 to 4 participants video is shown at the same time to save bandwith and computer power as the more videos are in a conference the more resources are needed. And each video adds exponentially to the load.
So whenever someone speaks, that video is shown. And if that participant goes silent for a while his video will not be transmitted to the others anymore.
We recommend Google Chrome Browser or Firefox, Safari is not supported.
You also need to enable camera, microphone and screen capture in your settings. Go to “System Preferences” -> “Security” -> “Privacy”. Allow Google Chrome to access “Camera”, “Microphone” and “Screen Capture”.
To set a password please click the information icon at the bottom right of your screen. This opens a popup screen similar to the one down below. To add a password please click add password. After doing this you can type a password. To confirm the password press enter on your keyboard.
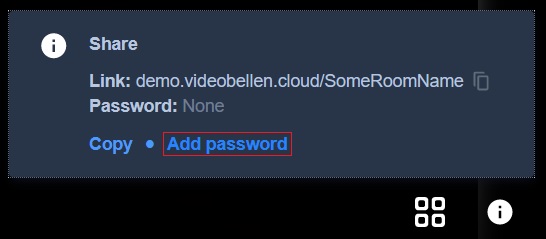
To cancel the password press cancel password.
This feature of Video Conferencing is to blur your background. It might have influence of your computers performance.
Of course, you can. Just move your cursor over to the bottom left of the browser screen and click open/close chat. This opens a chat window on the left side of your call. This can be used to send chat messages

Chat can also be opened by pressing C on your keyboard
Yes simply click the microphone icon at the bottom center of the browser to mute/unmute yourself.
Muting/unmuting your microphone can also be achieved by pressing M on your keyboard
To leave a call simply click the red phone icon at the bottom center of your browser.

There is a tile view that shows all participants in a tile formation. To use this simply press the four tiled icon at the bottom right of your browser. This view is great to see everyone if they are using a webcam, or to see multiple shared screens at once. You can also use W on your keyboard to enter and exit tile view.

To change your displayed name, click on the three dotted icon at the bottom right of your browser to open the menu shown below.

Then either click on the current name or Settings and navigate to the profile tab. On this tab you can change you displayed name, to confirm press Ok.

To change the video quality settings, click the three dotted icon at the bottom right of your browser and then click on Manage video quality. This opens a screen where you can select your preferred quality from Low bandwidth, Low definition, Standard definition, or High definition. After making you selection click Done to confirm it.


To make sure that only invited participants can enter the meeting room, you can set a password. Keep in mind: The meeting rooms are volatile, i.e. the password is only valid once you open the meeting and expires once you close it.
When you cannot hear other people in the conference, please make sure your audio works by playing some music or a video on Youtube. If that works please make sure that the tab of the meeting isn’t muted, you can check this by looking at the tab name in the upper side of your screen.
This session has been muted and can be unmuted by clicking on the speaker icon.
You can define the level of quality of the video stream that is sent to you from the server. Best is to try out different levels to see which one works best.
Open ‘more actions’ menu
Press the three dots in the bottom right corner.

Manage video quality
Chose “Manage video quality” from the menu.

Pick the quality level
Reduce the quality level. You can choose from the following options:
- High definition – this is the best quality but uses the most resources.
- Standard definition – the video is still qood but not as good as in High definition
- Low definition – the full screen video is quite blurry
- Low bandwidth – Audio only, no video is transmitted

The first person entering a meeting becomes host at the moment. So be early makes you host.
This behaviour will change if/when we have (strong) authentication for the host being put back in.
We didn’t answer your question? Get in touch with us via +31 888 SECURE (732873)
A meeting room is created as soon as you assign a name and activate the link generated on it. But there can only be one! Choose the name of your room so individually that it cannot be easily confused or quickly guessed. Ps. The meeting room is only valid once you open the meeting and expires once you close it.

F.e https://free.videoconferencing.services/kickoff-15-june
Of course, just simply click the hand icon on the bottom left of your browser to raise your hand. This shows the speaker that you would like to speak. To stop this simply click the hand again to lower it.
![]()
![]()
Simply click the camera icon at the bottom center of your screen to start/stop sharing your webcam
You can also start/stop your camera by pressing V on your keyboard
To share your entire screen or any open screen simply click the Screen icon at the bottom left of your browser.
Afterwards it will ask for permission and which screen you would like to share
After selecting a screen press allow to share the selected screen with all participants


To remove a password from your meeting first click the information icon at the bottom right of your browser. This opens a similar screen as shown in the image below. Then simply press remove password to remove the password and allow free access to your call/meeting.
To switch to full screen view, click on the thee dotted icon at the bottom right of your browser and then on view full screen. You can also use S on your keyboard to enter or exit full screen view.

-
Unified threat management
The term Unified Threat Management refers to a single (virtual) appliance typically used as a firewall that integrates the most common security solutions, including:
- Firewall
- (WiFi) Captive Portal
- Webfilter
- Intrusion Detection and Prevention
- Data Leakage Prevention
- Network Address Translation (NAT)
Most UTMs also include a VPN to connect to the network from your home computer or while on the go.
ID Control's web filter gives you the option to block dangerous websites, content and applications. For example, you can choose not to let your employees use social media so that they cannot be distracted.
You can filter by the following criteria:
- Time
You can set a filter in which you can set, for example, that the use of social media is not allowed during office hours - Location
You can block traffic to and from a particular place when this traffic has a higher classification of risk - Role of employees
You can create groups of employees that each have different restrictions and permissions - Active Directory integration
When the connector is installed on Windows, users can be easily adopted
Intrusion Alarm Systems (IDS) are systems designed to receive signals that indicate an intrusion into the network or the computer they are monitoring. ThreatControl's intrusion detection system targets incoming network traffic which it analyzes and compares against what is known as “good traffic” and when that does not match, generates a detection alarm.
When this alarm is generated, the connection is automatically disconnected, preventing further intrusion (prevention).
With our web filtering, you can choose to block specific websites or categories of websites based on certain characteristics such as the class of the website (news site, video site, photo site), geographic location, risk factor of websites (websites that offer illegal software downloads by torrents). use), and much more!
With the web filter module, statistics can be displayed about internet use, specific websites that the users go to are not shown, but you get an overview at the macro level of the websites that have been visited (for example, social media).
It is possible to implement strong authentication on the VPN access. You have to keep in mind that when you log in to the VPN you add the one-time password to your password. When you set up strong authentication, you can set whether the one-time password should be before or after your normal user password.
The ThreatControl UTM mini UTM requires that you have at least:
- 500 MHz CPU
- 512 MB RAM
- 4 GB SD card to install reduced system
Minimum specifications for full installation:
- 1 GHz dual-core CPU
- 1 GB RAM
- 40 GB SSD / HDD
- The full system installer requires a minimum of 1 GB RAM
Recommended specifications for full installation:
- 1,5 GHz multi-core CPU
- 4 GB RAM
- 120 GB SSD
A Virtual Private Network (VPN) is a technology that allows you to establish a secure network connection to a remote network, thereby making you part of that particular network. Consider, for example, your company network: If you have files on a server that you can only access when you are on location, you can use a VPN to set up a connection to that location so that you can still access your files remotely.
A firewall is a device that secures and monitors incoming and outgoing connections and usually serves as a bridge between the internal network and the Internet.
You can use Active Directory for authentication and authorization of (certain parts of the) management console. To do this, you need to add an LDAP server and add a user who can read the user information on the Active Directory side (bind user). You can then use this user to request user information from Active Directory.
It is possible to secure the administrator environment with strong authentication. You can use your favorite Authenticator app for this or an RFC 6238 compliant Time-based One Time Password token.
Email oplossingen
Not all emails sent need to be encrypted. Emails to be encrypted are emails containing confidential information.
Encrypted emails are available for 30 days from the date of sending.
Yes, SwitchMail supports all email environments including Exchange and Office365,
Yes, SwitchMail offers the most options for email encryption, decryption and digital signing. You can think of S / Mime, PGP, PDF Encryption and TLS.
SwitchMail Archiving provides the ability to place searches for messages, sender, recipients and even within attachments based on your archiving policy with reports. You can also bookmark these reports.
Yes, mail folders, contacts and calendars can be browsed.
Yes, every search result in SwitchMail Archiving can be exported in PDF format to serve as proof.
Yes, you can archive this email locally in the EU. You can then adjust the data retention policy at Google or Microsoft.
The ID Control Multi-Factor Authentication provides an extra layer of protection for the login recipients and users of Secure Email encryption or archiving by requiring them to use something they know (their password) and something they have (such as a mobile authenticator that provides one-time generated passwords).
Strong authentication can also be used for the sender, but a separate module must be purchased for this.
If you are using a one-time passwords App you can scan a “Software Token” using the QR code with your Authenticator app.
To send an encrypted email, simply enter the keyword [secure] (without brackets) anywhere in the subject line of the message. Note that you don't have to put spaces between the subject of the message and the tag [secure].
If you see the “Reply” link, it is because the sender of the message allows the recipients to reply to the message. If the recipient is allowed to reply to a message, the reply will be sent securely via SwitchMail.
The DLP module protects against accidental data breaches, but does not protect you from an experienced attacker. Any DLP vendor who claims to be able to detect all information leaks is not telling the full story.
Yes, you can send your mails using Office 365 encrypted with SwitchMail.
Tip: Also take a look at SwitchMail Archiving for Office365
Yes, you can grant multiple users or groups access to a shared mailbox.
Yes, the archive can be backed up, exported or restored in the mailbox. Even if you change mail environment you will not suffer from legacy.
Your email archive is located in the Netherlands or Europe in an ISO 27001 certified data center which is managed by ID Control as processor.
Almost all email servers and services are supported that organizations use.
You can use the following options:
– SMS (MessageID)
- OTP generating app such as (but not limited to) Google / Microsoft Authenticator, FreeOTP or Authy





